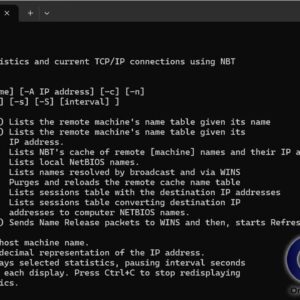
Have you ever wanted to know what computer belongs to what IP address? This information can come in very handy when trying to troubleshoot network issues or see if there are devices… Read More
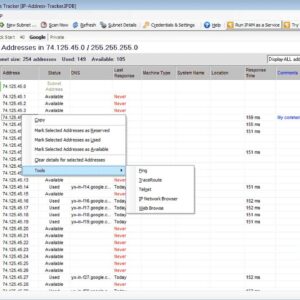
If you do IT (Information Technology) for a living you most likely know about IP addresses and know how they are configured in your environment. If you have hundreds or thousands of… Read More
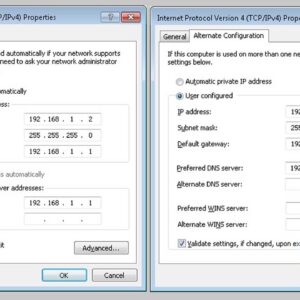
Dynamic IP addresses are IP addresses that change over time and are usually allocated automatically by a DHCP (Dynamic Host Configuration Protocol) server. These are common for workstations and home computers. Static… Read More

Ethernet is a standard of network communication using twisted pair cable although coaxial cable was used in older versions of Ethernet. Ethernet was developed in 1973 by Bob Metcalfe at Xerox. It… Read More
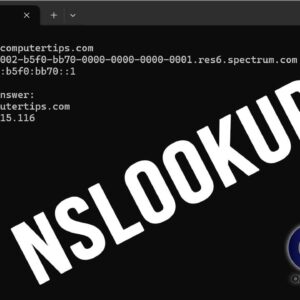
There are many command line networking tools that you can use to do various things from checking the connectivity of hosts on a network to finding out IP information about your computer.… Read More
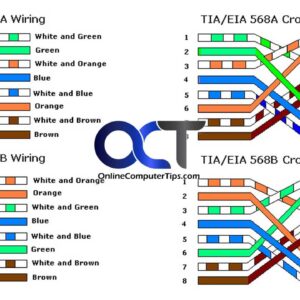
Ethernet cables, or as many people call them networks cables are used for data transmission between devices on a network. They consist of a cable with 4 pairs of wires connected by… Read More
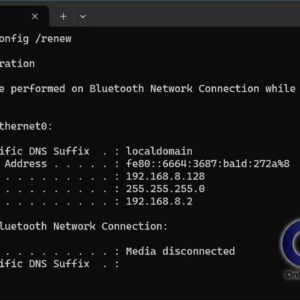
IP addresses are used on networks and on the Internet to allow computers to communicate with each other. If you don’t have an IP address on a TCP/IP based network then you… Read More
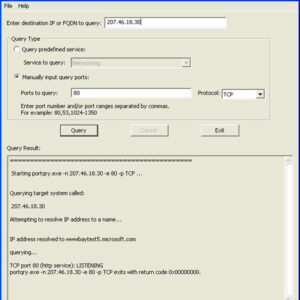
Ports are used in the computing world to tell a program or service where to go for its communications. There are different port numbers assigned to various services. These ports allow applications… Read More
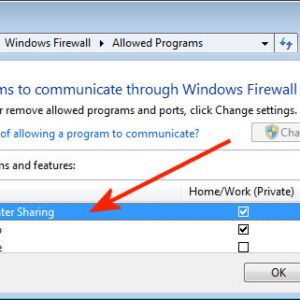
Wi-Fi hotspots offer a wonderful solution to those on the move; these hotspots help people to stay connected to the net while they are away from their homes or offices. At the… Read More
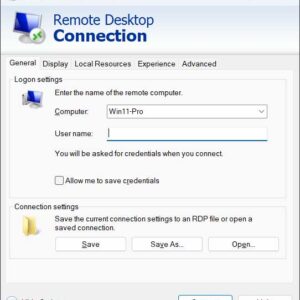
Now that many people have multiple computers at home and at the office they are realizing how handy it is to be able to connect to other computers on the network or… Read More
