Securing sensitive data is becoming increasingly critical for Windows users, whether you’re a home user, an IT professional, or a small business owner. Microsoft offers two built-in options: BitLocker and Device Encryption. While they share some common goals, these tools differ significantly in features, compatibility, and control. In this article we will be discussing the differences between Windows BitLocker and Device Encryption so you know which one you can use on your computer and to also help you decide if you want to implement this feature at all.
Why Does Encryption Matter?
Before diving into technical differences, it is worth understanding why encryption is essential:
- It protects your data if your laptop is stolen or your drive is removed and accessed elsewhere
- Defends against malware or unauthorized users accessing files
- Ensures compliance with work or school IT policies
- Dramatically increases protection against data theft or unauthorized drive access
What Is BitLocker?
BitLocker is Microsoft’s full-featured drive encryption technology, targeted at users needing advanced security and control. It’s available in Windows Pro and Enterprise editions.
Key Features:
- Full Drive Encryption: Encrypts entire system and additional internal or external drives.
- BitLocker To Go: Protects removable USB drives.
- TPM Integration: Uses Trusted Platform Module to safeguard encryption keys, often allowing seamless bootup.
- PIN & Startup Key Options: Adds a pre-boot PIN or USB startup key for extra security.
- Automatic Device Lockdown: Prevents access if tampering is detected.
- Multiple Recovery Key Options: Can store keys in Microsoft accounts, Azure AD, Active Directory, USB, or printed copies.
- Group Policy Support: Admins can enforce encryption in business settings.
Ideal For:
- IT technicians
- Small businesses
- Advanced users wanting strong encryption controls
What Is Device Encryption?
Device Encryption offers a simplified approach, designed for standard consumer protection. It’s found in Windows Home editions on supported hardware.
Key Features:
- Automatic Encryption: System drive is encrypted automatically when signed in with a Microsoft account (sometimes without obvious notification).
- One-Touch Key Backup: Recovery key is stored with your Microsoft account.
- Minimal User Interaction: Enabled only on devices with modern standby and TPM 2.0.
- Not enabled when using a local user account.
- Can be disabled in the Windows settings under Privacy & security.
- Once disabled, the recovery key stored in your Microsoft account is no longer needed.
Limitations:
- No BitLocker To Go (USB encryption)
- Can’t encrypt additional drives, add PIN/startup keys, or customize policies
- No group policy support or fine-tuning options
Best For:
- Home users or those with daily-use laptops
- Users wanting basic, hands-off protection against theft
Here is a table showing the main differences between BitLocker and Device Encryption.
| Feature | BitLocker | Device Encryption |
| Full system drive encryption | Yes | Yes |
| Encrypt additional drives | Yes | No |
| BitLocker To Go (removable USB) | Yes | No |
| Requires TPM 2.0 | Yes | Yes |
| Pre-boot PIN / Startup Key | Yes | No |
| Policy customization | Yes | No |
| Group policy support | Yes | No |
| Recover key storage options | Microsoft/AD/USB/Print | Microsoft account |
How to Enable BitLocker on Windows Pro Edition:
- Access BitLocker via Control Panel.
- To enable, choose recovery key backup method (Microsoft account, file, print). Backups should NOT be stored on the encrypted drive.
- Choose to encrypt used space only (faster) or entire drive (more thorough).
- Select the encryption mode: default (best for new PCs) or compatible (for older versions).
- Encryption time varies by drive size; computer can be used during the process.
- After encryption, BitLocker can be suspended for hardware changes without decrypting.
- Recovery keys can be backed up later (to another method if desired).
- BitLocker To Go can be used for USB drives, with password or smart card protection.
- After restarting, drives using TPM don’t require a key each time unless hardware changes occur.
BitLocker Configuration Demo:
To enable BitLocker in Windows, open Control Panel and then double click on BitLocker Drive Encryption. If BitLocker is disabled, you will have the option to enable it by clicking on Turn on BitLocker. If you have a secondary hard drive, you will see the option to enable BitLocker to Go.
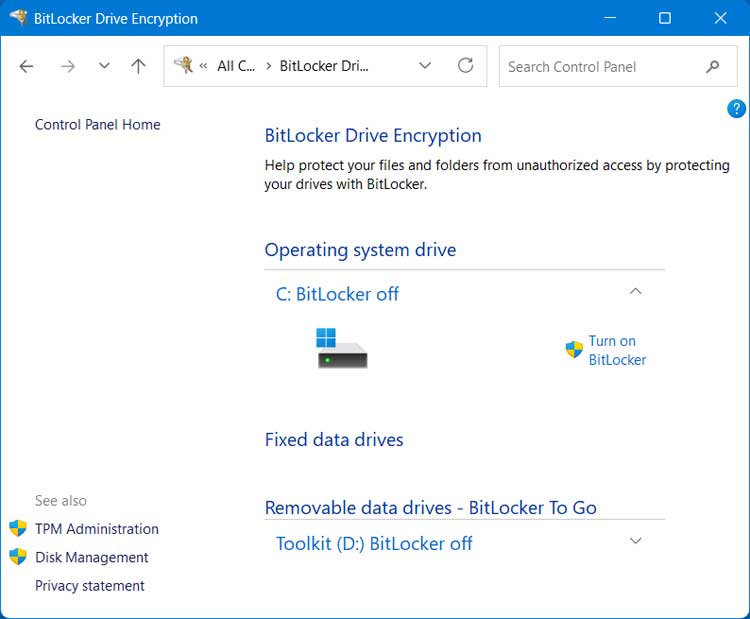
You will then need to choose where you want to backup your recovery key. Whichever method you choose, make sure you will not lose access to this key otherwise you may not be able to get to your files if you run into a situation where it’s needed such as moving the drive to a different computer.
When you save your BitLocker recovery key to your Microsoft account, it’s securely stored online and linked to your account credentials. You can also save it as a text file on a different drive or external hard drive or flash drive. You can also print it on a sheet of paper but be sure to keep it in a safe place.
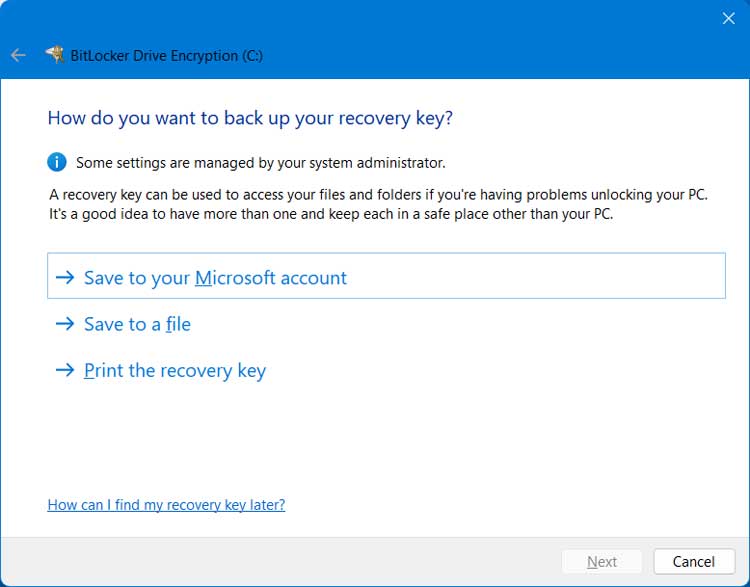
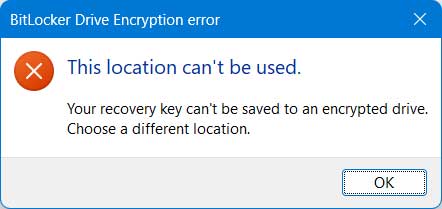
If you choose the save to a file option and try and save it on the same drive you are encrypting, you will get a message saying “Your recovery key can’t be saved to an encrypted drive. Choose a different location”.
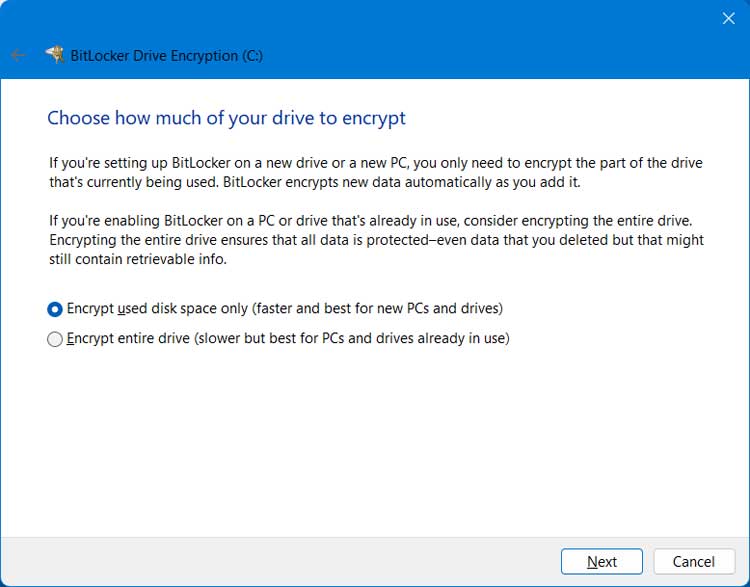
You will then have the option to encrypt only the used disk space or the entire drive. If you choose the first option, it doesn’t mean that it will only encrypt the current files and nothing else because as you add new data, it will get encrypted as well.
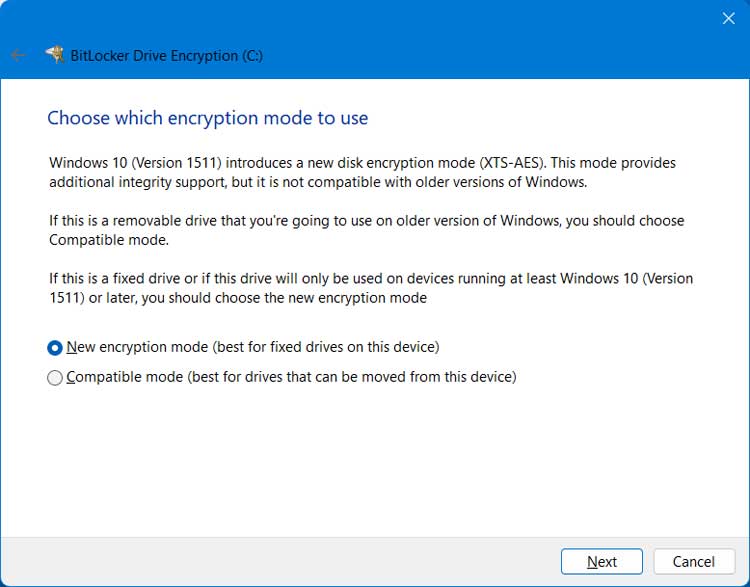
If you are not planning on using this drive on an older version of Windows, you should use the new encryption method for the best results. New encryption mode uses the stronger XTS‑AES algorithm but only works on Windows 10/11 systems. Compatible mode uses the older AES‑CBC algorithm, which is less secure but allows the drive to be read on older versions like Windows 7/8.1.
Next, you will have the option to run the BitLocker system check which is a test that restarts your PC to confirm it can correctly read the encryption key from the TPM and boot into Windows. If the check passes, BitLocker begins encrypting the drive; if it fails, encryption won’t start so you don’t get locked out.
Once you are ready to begin the encryption process, you can click on the Start encrypting button. How long this process takes will depend on the size and speed of your hard drive.
Once the encryption process is complete, you will see a message telling you so.
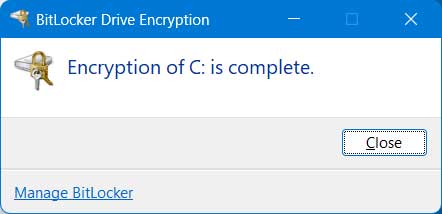
Now when you go back to the BitLocker settings, you will see that it says that BitLocker is on and you will have some options to suspend protection which is used when you need to temporarily turn off BitLocker’s security checks without fully decrypting the drive which can be used for things such as installing firmware or BIOS updates or making hardware changes so you can keep the drive encrypted but avoid being locked out. You can also back up your recovery key again using a different method if needed.
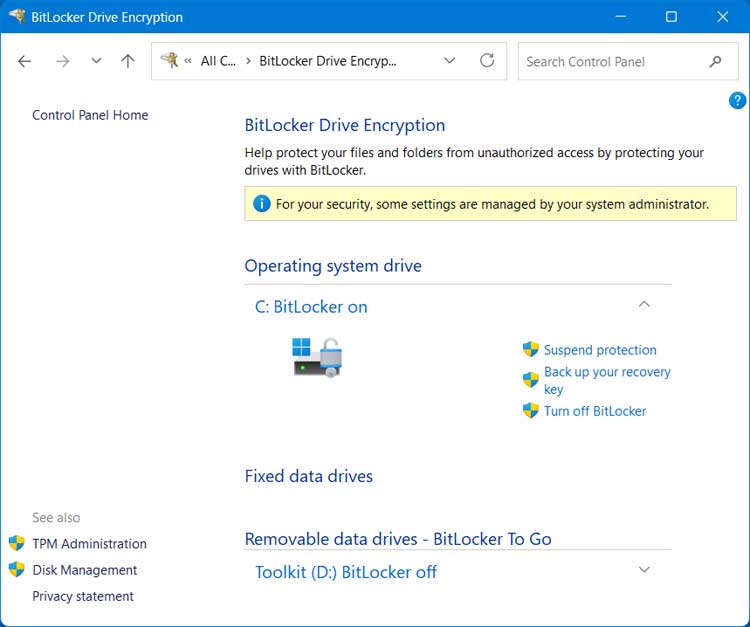
The message that says “For your security, some settings are managed by your system administrator” is normal because Windows automatically locks certain security options using built‑in policies. Even if you’re the only user on a standalone PC, the system itself acts as the “administrator” to enforce those rules, so it shows the warning to let you know some settings can’t be changed for your protection.
How to Device Encryption on Windows Home Edition:
- BitLocker isn’t available.
- Device Encryption requires compatible hardware: modern standby, TPM 2.0, Secure Boot.
- On unsupported devices, you won’t see Device Encryption in settings.
- When available, find it under Settings > Privacy & Security > Device Encryption.
- Typically, Device Encryption activates automatically with a Microsoft account.
Which Should You Use?
- Choose BitLocker if you need full control, want to encrypt additional drives, use business group policies, or require advanced recovery options.
- Choose Device Encryption if you want effortless, basic protection for a Home edition device that’s compatible and you’re signed in with a Microsoft account.
Recommendations:
- Check Device Compatibility: Not all hardware supports Device Encryption; verify system support via Windows settings and system information.
- Backup Recovery Keys Securely: Make sure to store recovery keys somewhere safe and consider physical copies for maximum security.
- Consider Your Use Case: Business environments, tech power users, and those with multiple drives should use BitLocker. Home users who don’t require advanced controls are usually fine with Device Encryption.
Conclusion:
Both BitLocker and Device Encryption significantly enhance your Windows device security. BitLocker offers granular control and broader capabilities for professional and enterprise users; Device Encryption delivers easy, automatic protection for most everyday consumers. Evaluate your system’s compatibility and your personal security requirements before deciding which is best for you. There are also standalone apps you can use to encrypt individual files and folders.
For additional training resources, check out our online IT training courses.
Check out our extensive IT book series.