
Ever since Windows 11 came out, many people have been complaining about how it’s not as customizable as Windows 10 and can be a bit buggy depending on what version you are… Read More

In the current online environment, having a robust domain reputation is crucial for fostering trust, facilitating secure communications, and ensuring successful email delivery. Cybersecurity threats such as spoofing and phishing are constantly… Read More
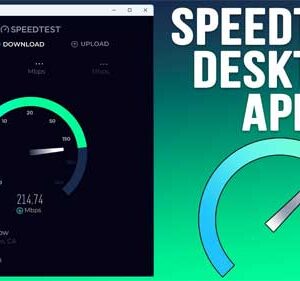
These days, everyone has a super fast internet connection and the days of slow dial up internet are long gone (thankfully!). But how do you know if you are getting the download… Read More
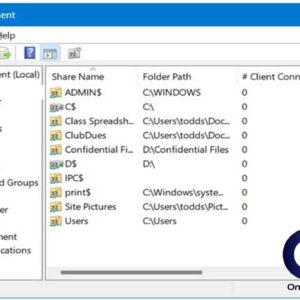
Sharing files and folders is nothing new for Microsoft Windows users. If you have a home or office network, you can easily share folders so other people can access your files from… Read More

Sharing files and folders in Windows is nothing new and you may have configured some shared folders and printers on your computer at some point. And you might have also noticed that… Read More
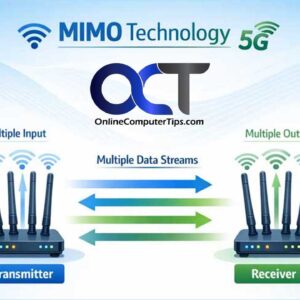
MIMO stands for Multiple Input Multiple Output, a wireless communication technology that uses multiple antennas at both the transmitter and receiver ends to improve data throughput and reliability. Unlike traditional single-antenna systems,… Read More

Networking with Microsoft Windows has been a popular way to share files and folders at the office and even at home since the early days of Windows itself. When you share a… Read More

In the contemporary landscape dominated by digital communication, email plays a crucial role in the functioning of businesses. From marketing initiatives and transactional correspondence to internal messaging, companies depend significantly on a… Read More
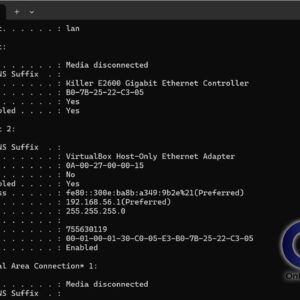
When it comes to network administration, you need to know some of the more common networking commands to successfully manage your network. Sure, there are plenty of built in Windows tools that… Read More

These days, many people use their smartphones more than their computers when it comes to things such as checking email, browsing the internet and social media. But if you are the type… Read More
