Windows 2000 and higher versions allow you to adjust the local security settings for a particular computer. If the computer was part of a domain on a network then these settings would most likely be set at the domain group policy level on a domain controller. If you are not part of a domain or if you are a single computer user then you can adjust your security settings so that they affect the users of your computer or computers.
To edit the standard security policy of a Windows computer you can use the Local Security Settings tool or the Group Policy Editor tool. The Local Security Settings tool will show you only items related to the security of that computer while the Group Policy Editor tool will show you additional items you can configure such as user and software settings.
To open the Local Security Policy click on Start, Programs and then Administrative Tools. Then you will have a Local Security Policy icon within the Administrative Tools group. If you don’t have the Administrative Tools group showing then right click your taskbar and choose Properties. From there click on the Start Menu tab and then the Customize button. If you use the Classic start menu check the box that says Display Administrative Tools. If you use the regular start menu then click on the Advanced tab scroll down to System Administrative Tools and check Display on the All Programs menu and the Start menu. For newer versions of Windows right click the taskbar and choose Properties. Then go to the Start Menu tab and click on Customize. Scroll down to System administrative tools and check the radio button that says Display on the All Programs menu. Now you will have an Administrative Tools option under your Programs menu. Now you can click on Local Security Policy. Another easier way to get to the Local Security Policy is to click on Start and then in the Run box or the Vista or Windows 7 search box and type in gpedit.msc.
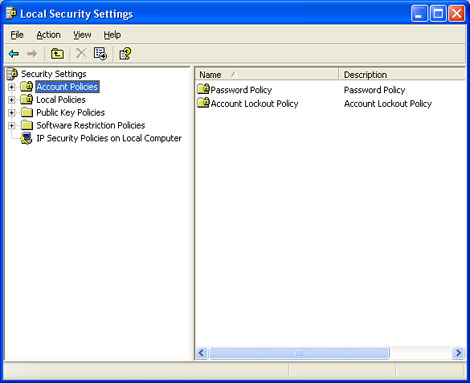
You will see several sections related to different areas of the security policy.
Account Policies is where you can set password policies such as the minimum password length and how long before passwords expire. You can also setup account lockout policies which can lock out a user if they enter the wrong password too many times.
Local Policies is where you setup things such as auditing for logins, file access, policy changes and other type of events that can be logged. There is also a section for user rights assignments which allows you to fine tune what administrative tasks your users can perform. In the Security Options section you can grant or deny various rights such as the ability to rename the administrator account and restricting access to devices such as the CDROM.
Public Key Policies is used to specify how to manage certificates and certificate life cycles. This security setting specifies whether certificates are automatically enrolled, renewed when they are expired, and removed when they are revoked.
Software Restriction Policy is used as a way to identify software and control its ability to run on local computers. The two security levels are Disallowed and Unrestricted.
IP Security Polices (IPSEC) is a framework for a set of protocols for security at the network layer of network communication. It is used to support secure exchange of packets at the IP layer and is widely used in Virtual Private Networks (VPNs). Windows has 3 built in IPSEC polices. Client, Secure Server and Server. Client (Respond Only) is used to negotiate with servers that request security but its not necessary to use security if none is present. Secure Server (Require Security) does not allow unsecured communication with untrusted clients. Server (Request Security) always requests security but allows unsecured communication with clients that do not respond to request.
Newer versions of Windows will have additional areas that you can configure.
Windows Firewall with Advanced Security is where you can set firewall settings to secure network traffic.
Network List Manager Policies which oversees the identified and unidentified networks.
Application Control Policies which allows you to control how users can access and use files.
Advanced Audit Policy Configuration where you can audit various events on your network or domain such as logons and logoffs or object access.