Once again it’s time for a Microsoft security breach that has the possibility of making your life miserable. The Russian hacking group Fancy Bear (or APT28) has found a flaw in Microsoft Office documents that can allow malware to be installed just by opening a document on your computer. This has been going on since late October and the subjects of the documents are related to US Army exercise in Eastern Europe known as SabreGuardian and the ISIS New York truck attack.
The Microsoft’s Dynamic Data Exchange feature is designed to allow Office files to include links to other remote files and that’s all that’s needed to get the malware installed. It will usually ask the user if they want to update links from the remote file. The files are known to have names such as SabreGuard2017.docx and IsisAttackInNewYork.docx. Microsoft PowerShell scripting is used to install the malware called Seduploader on the users machine.
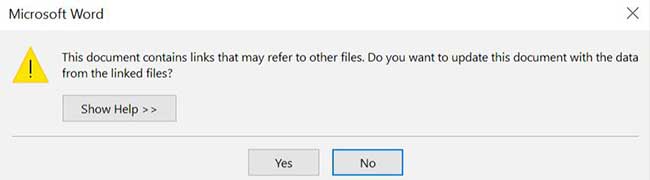
Microsoft doesn’t consider this a flaw on their end and say the software is working as intended but that people need to be more careful when opening files from un trusted sources. Even if it’s from someone you know you should always be careful when opening email attachments especially if its forwarded from someone else rather than being a new email.